
Related products
-
DC EDR End-Points
Categories: Services, Cyber Defense, SOC in box -
-
DarkNet Leaked Data Monitoring
Categories: Services, DRP Intelligence, SOC in box

SSL/TLS Penetration Testing

Vulnerability Scanner Package

Asset Inventory Package

Internal Network Pentest

Web Server Pentest

Web Application Pentest

DLP Project

DC Agent

3D World Maps

Entity Relation Mapping

Analytics & Charts

Interface

Real-time Risk Dashboard

Instant Reports of Incidents

Breach Warranty

Real-time External Risk Dashboard

Continuous Red Teaming

Real-Time Afflicted Exploit Watch

Automated Surface Recon

Virtual CISO

Infrastructure & Network Design Security Review

Hardening Guidelines Current Capabilities Assessment

Phishing Campaigns

Blackbox Internal Assessment – Network

Blackbox External Assessment – Web

Blackbox External Assessment – Network

Red Team engagement

DarkNet Leaked Data Monitoring

External Deception

Brand Monitoring / Executive Protection.

Ransomware Prevention

Compromise Recovery with Zero Downtime

Compromise Detection

Incidents Monitoring

Threat Hunting & Detection

Incident Response and Remediation

Cyber Monitoring
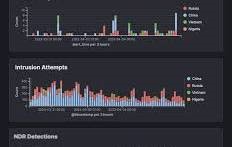
DC NDR

Threat Hunt

Attack Projectory

DFIR for Incident Response

DC EDR End-Points

Web Security/WAF

XDR

Cyber Defense
EGP30,000
Research and Development

Zero Client

Customized ERP System

Web Development

Cyber Insurance
SOC in Box

PENETRATION TESTING SERVICES
EGP30,000
Forcepoint Firewall

FortiGate Firewall

Motivational Book Cover
This story, dazzling in its powerful simplicity and soul-stirring wisdom, is about an Andalusian shepherd boy named Santiago who travels from his homeland in Spain to the Egyptian desert in search of a treasure buried near the Pyramids. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt etc.
3 in stock

SSL/TLS Penetration Testing

Vulnerability Scanner Package

Asset Inventory Package

Internal Network Pentest

Web Server Pentest

Web Application Pentest

DLP Project

DC Agent

3D World Maps

Entity Relation Mapping

Analytics & Charts

Interface

Real-time Risk Dashboard

Instant Reports of Incidents

Breach Warranty

Real-time External Risk Dashboard

Continuous Red Teaming

Real-Time Afflicted Exploit Watch

Automated Surface Recon

Virtual CISO

Infrastructure & Network Design Security Review

Hardening Guidelines Current Capabilities Assessment

Phishing Campaigns

Blackbox Internal Assessment – Network

Blackbox External Assessment – Web

Blackbox External Assessment – Network

Red Team engagement

DarkNet Leaked Data Monitoring

External Deception

Brand Monitoring / Executive Protection.

Ransomware Prevention

Compromise Recovery with Zero Downtime

Compromise Detection

Incidents Monitoring

Threat Hunting & Detection

Incident Response and Remediation

Cyber Monitoring

DC NDR

Threat Hunt

Attack Projectory

DFIR for Incident Response

DC EDR End-Points

Web Security/WAF

XDR

Cyber Defense
EGP30,000
Research and Development

Zero Client

Customized ERP System

Web Development

Cyber Insurance

SOC in Box

PENETRATION TESTING SERVICES
EGP30,000
Forcepoint Firewall

FortiGate Firewall

Motivational Book Cover
This story, dazzling in its powerful simplicity and soul-stirring wisdom, is about an Andalusian shepherd boy named Santiago who travels from his homeland in Spain to the Egyptian desert in search of a treasure buried near the Pyramids. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt etc.
3 in stock

SSL/TLS Penetration Testing

Vulnerability Scanner Package

Asset Inventory Package

Internal Network Pentest

Web Server Pentest

Web Application Pentest

DLP Project

DC Agent

3D World Maps

Entity Relation Mapping

Analytics & Charts

Interface

Real-time Risk Dashboard

Instant Reports of Incidents

Breach Warranty

Real-time External Risk Dashboard

Continuous Red Teaming

Real-Time Afflicted Exploit Watch

Automated Surface Recon

Virtual CISO

Infrastructure & Network Design Security Review

Hardening Guidelines Current Capabilities Assessment

Phishing Campaigns

Blackbox Internal Assessment – Network

Blackbox External Assessment – Web

Blackbox External Assessment – Network

Red Team engagement

DarkNet Leaked Data Monitoring

External Deception

Brand Monitoring / Executive Protection.

Ransomware Prevention

Compromise Recovery with Zero Downtime

Compromise Detection

Incidents Monitoring

Threat Hunting & Detection

Incident Response and Remediation

Cyber Monitoring

DC NDR

Threat Hunt

Attack Projectory

DFIR for Incident Response

DC EDR End-Points

Web Security/WAF

XDR

Cyber Defense
EGP30,000
Research and Development

Zero Client

Customized ERP System

Web Development

Cyber Insurance

SOC in Box

PENETRATION TESTING SERVICES
EGP30,000
Forcepoint Firewall

FortiGate Firewall

Motivational Book Cover
This story, dazzling in its powerful simplicity and soul-stirring wisdom, is about an Andalusian shepherd boy named Santiago who travels from his homeland in Spain to the Egyptian desert in search of a treasure buried near the Pyramids. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt etc.
3 in stock

Customer Reviews
There are no reviews yet.